If your web application or website has public-facing API endpoints, such as contact forms, support requests, or login pages, bot traffic can quickly become a serious problem. When unchecked, automated API calls from bots can:
- Overload your server and database, and potentially crash your website
- Slow down the app for real users
- Trigger unnecessary workflows (e.g., support tickets)
- Inflate operational costs
- Skew analytics and decision-making
To maintain a seamless and secure experience for users, it’s critical to implement bot detection and prevention strategies using tools like filters, rate limiting, reCAPTCHA, and firewalls.
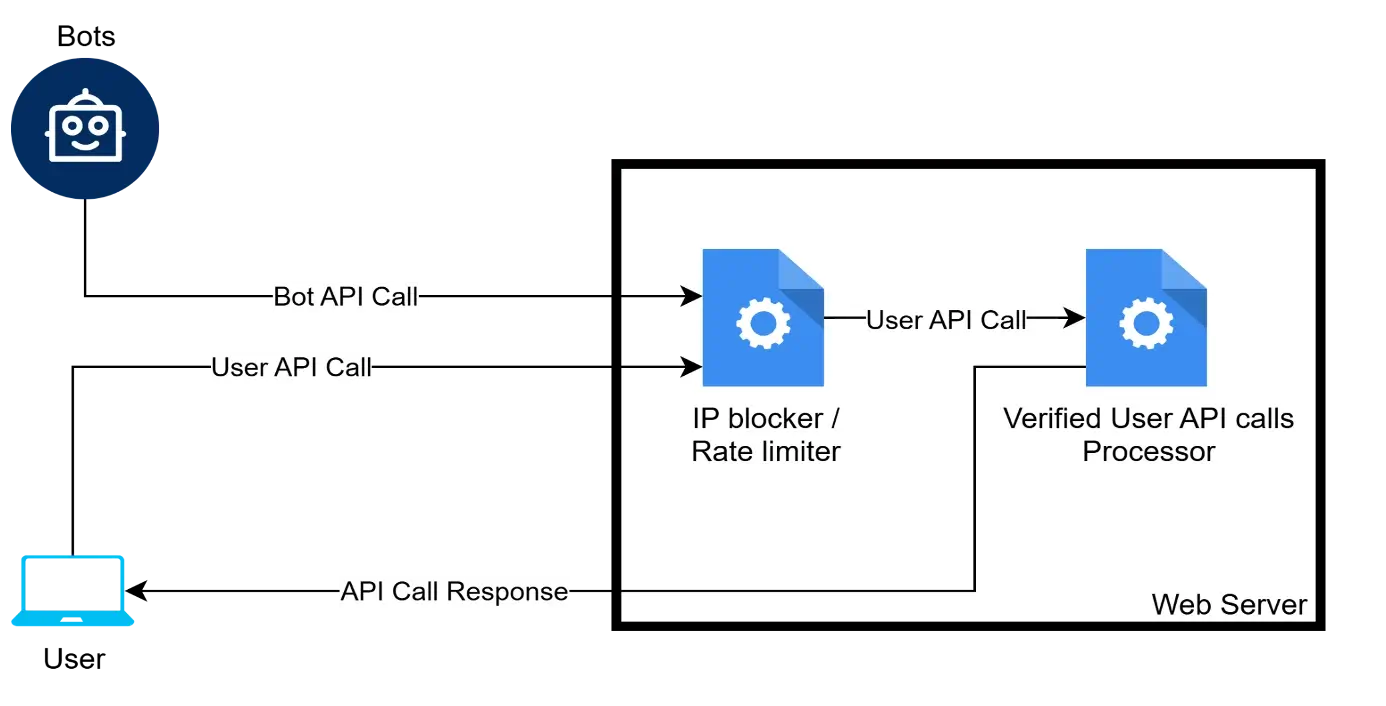
OPTION 1: Block Bot Traffic Using IP Filters and Rate Limiting
This is the simplest and most direct method. You can use custom logic or server-level configurations to block suspicious IP addresses or limit excessive API calls. The only caveat is that your bot traffic must be predictable, which is extremely difficult in today’s digital age. Modern bots will assume a new IP address and resume their activities.
Pros:
- Easy to implement
- Useful for blocking basic, unsophisticated bots
- Can be combined with user behavior heuristics
Cons:
- IP addresses can be spoofed indefinitely when blocked
- Legitimate users behind shared IPs may be misclassified
- Filtering happens on the app server, adding potential load when under attack by bots
Best for:
Low- to medium-scale bots where performance impact is minimal.
Common Solutions:
- Custom logic in application code
- Web server configs (Apache/Nginx)
- WordPress anti-bot plugins, such as Akismet
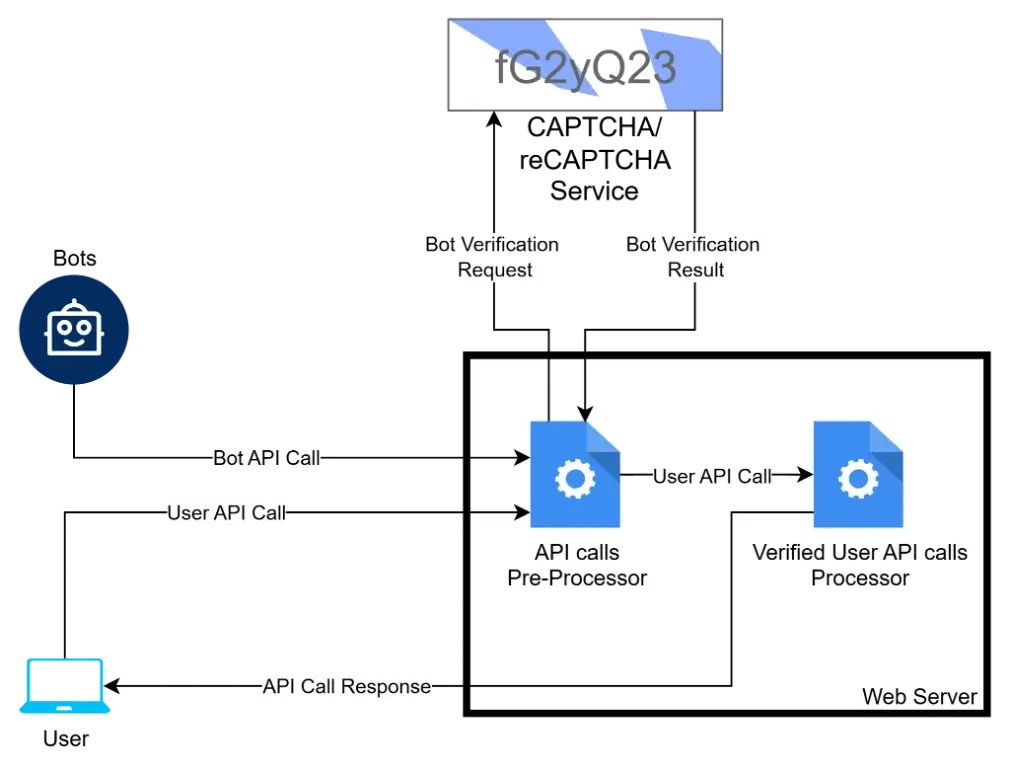
OPTION 2: Add reCAPTCHA for External Verification
Google reCAPTCHA is a powerful, low-latency way to distinguish between real users and bots. It integrates seamlessly into modern apps and websites, with minimal user friction. For WordPress, it’s usually done through a plugin and requires a secret and site key from Google.
Implementation Models:
1. Inline Server Verification
- Verifies reCAPTCHA tokens inside the main application process
- Suitable for most small to medium apps and websites
2. Dedicated Verification Server
- Offloads verification to a separate microservice
- Ideal for high-volume apps and websites where bot traffic is impacting server performance
Pros:
- Highly effective against bot traffic
- Minimal impact on user experience (mostly invisible to users)
- Scalable architecture options
Cons:
- Still relies on your server (unless offloaded)
- Will impact your pagespeed and SEO
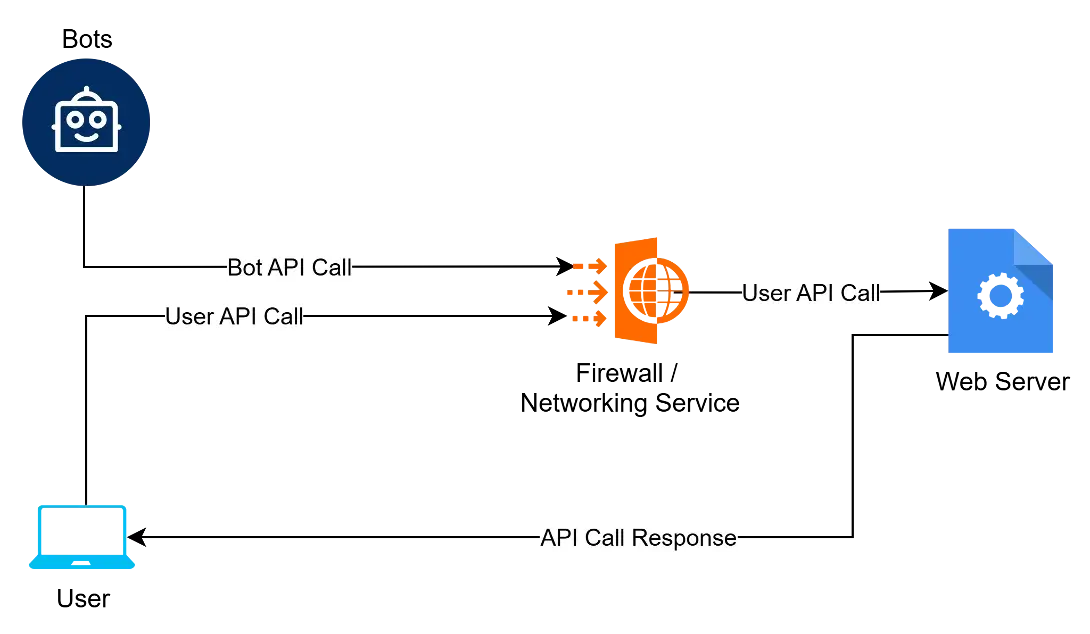
OPTION 3: Use Firewalls & Network-Level Protection
For enterprise-level protection, web application firewalls (WAFs) and network filtering services offer robust defense against bot attacks and DDoS attempts.
These services act as a protective layer before any traffic hits your application server. These services do so by identifying bot patterns through machine learning and blocking bot traffic before they reach your website.
Pros:
- Blocks bot traffic before it hits your app or website
- Reduces server load
- Centralized rule management
- High detection rates for sophisticated bots
Cons:
- Premium solutions can be costly
- Self-hosted options require ongoing maintenance
Popular Services:
Summary: Choose the Right Tool for Your App or Website
| Method | Best Use Case | Key Benefit |
| IP Blocking + Rate Limiting | Small-scale apps, websites, simple bot traffic | Easy to implement |
| reCAPTCHA | General apps, websites, public forms | Smart filtering, low user friction |
| Firewall / WAF | Enterprise-level apps, websites, high bot volume | Blocks traffic before server access |
Final Thoughts
Securing your application against bot traffic isn’t just a best practice; it’s essential for performance, user trust, and business continuity. Combining tools like reCAPTCHA, rate limiting, and a robust firewall gives your app multi-layered protection.
If your website or app is being bogged down by bot traffic, we can help! Contact Uplancer today for a free consultation.